Networking Pioneers, Settlers and Town Planners
Can we broadly separate Networking into Pioneers, Settlers, and Town Planners? I’ve been thinking about how to apply Simon Wardley’s PST model to networking. This leads to thinking about how we can encourage networking evolution. The model needs a lot of fleshing out, but I’m interested in what others think.
Pioneers, Settlers and Town Planners (PST)
Simon Wardley has written about “Pioneers, Settlers and Town Planners (PST)” in many places - e.g. here and here. It derives from Cringely’s Commandos, Infantry, Police model (see Chapter 12 of Accidental Empires). It provides a organisational structure, grouping areas based upon their current state of evolution. It recognises that no one operational model works for all parts of a business. You can’t say “We’re using Agile, or Lean, or Six Sigma” - you need to use the appropriate model for each area. Even “Bi-Modal IT” is too limiting, as the divide is too great.
(Image from blog.gardeviance.org, used under Creative Commons License)
Applying PST to networking
The model is a helpful way of thinking about the role of different groups across a business. It also helps us understand why teams need to evolve over time, as their area evolves. But what about networking? Can we apply this model to networking? I’ve been thinking about the different areas of networking are, how to identify them, and how to encourage evolution of ideas.
Wardley’s model is aimed at organisations trying to group their internal teams. The problem with applying this to networking is that most network teams are too small to be able to organise along that model. So maybe we need to look at it across the industry, and categorise both organisations and teams?
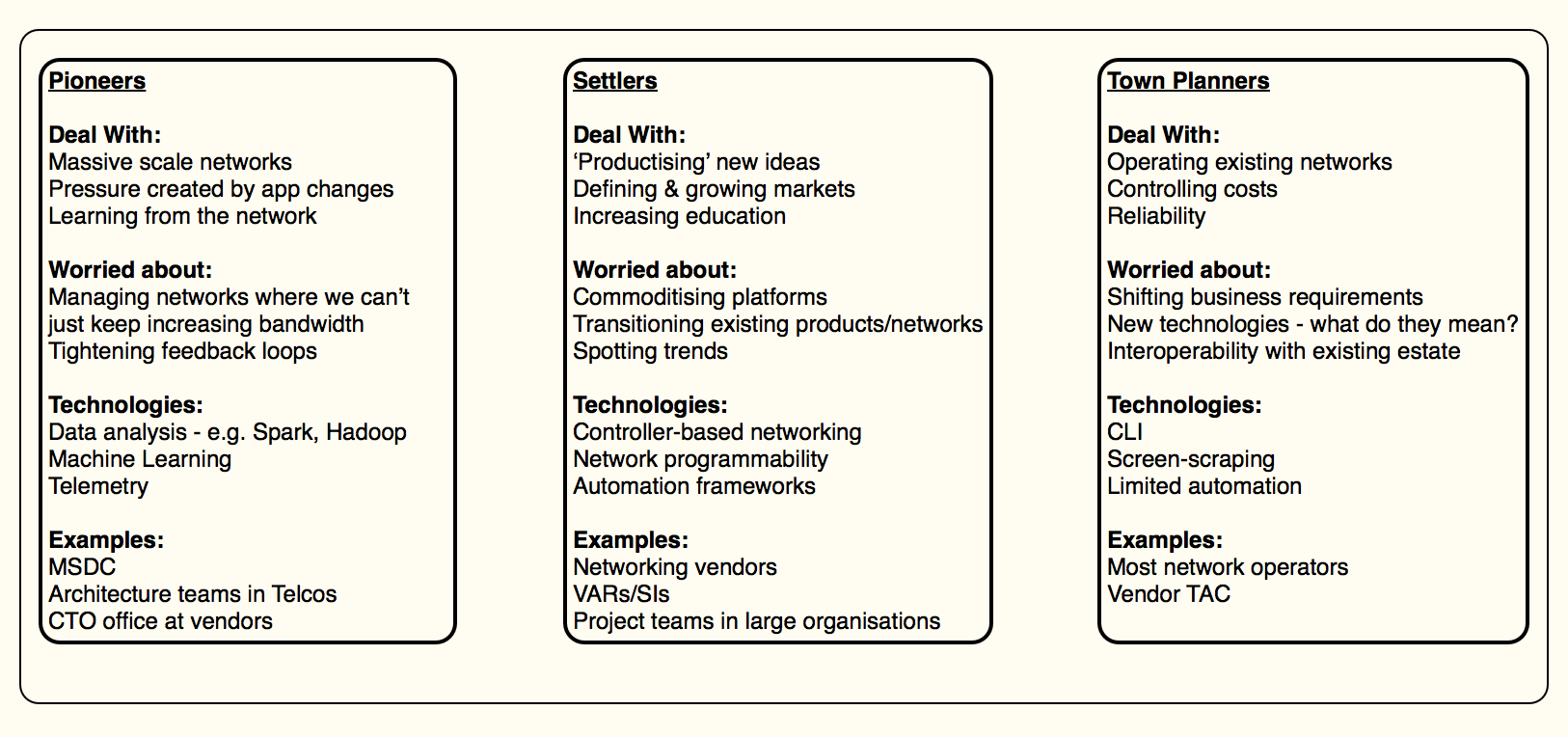
Here’s my first attempt at classifying networking into Pioneers, Settlers & Town Planners:
(No, it doesn’t directly map to the broader PST model. Suggestions for enhancements welcome.)
Sometimes Stealing is OK
‘Theft’ is a key part of the PST model:
The process of theft is essential to mimic outside evolution. All the components are evolving due to supply and demand competition which means new teams need to form and steal the work of earlier teams i.e. the settlers steal from the pioneers and the outside ecosystems and productise the work. This forces the pioneers to move on. Equally the town planners steal from the settlers and industrialise it, forcing the settlers to move on.
What does this mean in the context of networking? What does this ‘theft’ look like? Here’s some examples:
- Settlers stealing from pioneers: Pioneers will think about Machine Learning, and develop some of the pieces for collecting & processing data. Settlers steal those ideas, and put them into a usable package for solving a specific networking problem.
- Town planners stealing from pioneers: Town Planners see how the Settlers solved a specific problem, and made Machine Learning ‘real.’ Town Planners take that and expand the scope to cover more general problem sets.
- Pioneers learning from Town Planners: Pioneers will look at the information gained by applying Machine Learning to network data. They will then go further with that information, using it to drive the development of higher order systems.
This sort of ‘theft’ is critical for evolution. Yes, I work for a vendor, but I want to improve networking as a whole. What can we do to enable this theft?
- Recognise the role each group plays. None are better or worse, they are simply different roles.
- Make sure the other groups know what’s going on - so that could mean that the Pioneers hold regular sessions with the Settlers, showing them what they’re up to. On an industry-wide basis, we see some of this at conferences - e.g. Google talking about their challenges and requirements at the recent ONS conference.
- Don’t just dump things on the other groups - recognise their challenges. So products coming out of vendors need to provide a way to transition from current networking models.
This is where we can all play a part - blue-sky thinkers, network vendors, network operators.
The above is an imperfect model. You can poke holes in it and find counter-examples. It needs further fleshing out. But what do you think? Is this is a useful way of thinking about networking and states of evolution? What can we do to stimulate further theft and evolution?